Teacher
Professional
- Messages
- 2,669
- Reaction score
- 819
- Points
- 113
How do hackers sit unnoticed in the victim's systems, and where are all the protection tools?
The UNC4210 group attacked the systems of a European non-governmental organization using TinyTurla-NG malware to install a backdoor. A report on this cyberattack was published by Cisco Talos.
During the attack, hackers compromised one of the systems of an unnamed NGO, provided themselves with permanent access and added exceptions for antivirus programs to avoid detection. UNC4210 then used additional communication channels through the Chisel program to steal data and move to other available systems on the network.
It turned out that the first penetration into the systems occurred back in October 2023, while Chisel was deployed in December 2023, and data exfiltration occurred in January.
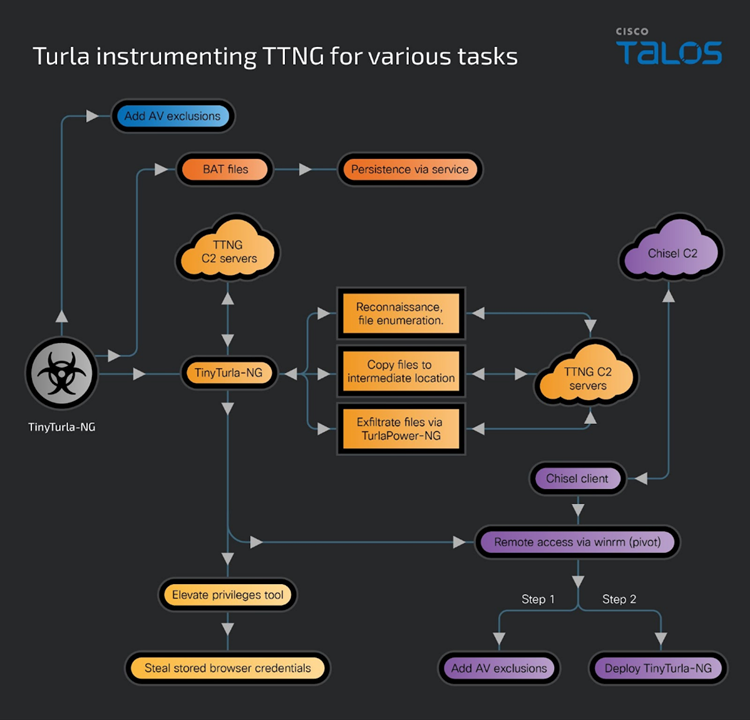
Turla Infection Chain
During the attack, UNC4210 used its initial access to configure Microsoft Defender antivirus exceptions to evade detection, and installed TinyTurla-NG, which is then saved by creating a malicious " sdm "service masquerading as "Device Manager".
The malware in this case acted as a backdoor, allowing cybercriminals to conduct intelligence, exfiltrate files to the C2 server, and deploy a modified version of the Chisel tunneling program. The path of penetration is still being studied.
As soon as attackers gain access to a new system, they repeat their actions, creating exceptions for Microsoft Defender, installing malware and ensuring its constant activity in the system.
At the end of 2023, TinyTurla-NG was already detected in the networks of Polish NGOs. At that time, Cisco Talos specialists stated that the virus spread through compromised WordPress sites that are used as a command and control server (Command and Control, C2). TinyTurla-NG can execute commands from a C2 server, upload and download files, and deliver scripts to steal passwords from password management databases.
The UNC4210 group attacked the systems of a European non-governmental organization using TinyTurla-NG malware to install a backdoor. A report on this cyberattack was published by Cisco Talos.
During the attack, hackers compromised one of the systems of an unnamed NGO, provided themselves with permanent access and added exceptions for antivirus programs to avoid detection. UNC4210 then used additional communication channels through the Chisel program to steal data and move to other available systems on the network.
It turned out that the first penetration into the systems occurred back in October 2023, while Chisel was deployed in December 2023, and data exfiltration occurred in January.

Turla Infection Chain
During the attack, UNC4210 used its initial access to configure Microsoft Defender antivirus exceptions to evade detection, and installed TinyTurla-NG, which is then saved by creating a malicious " sdm "service masquerading as "Device Manager".
The malware in this case acted as a backdoor, allowing cybercriminals to conduct intelligence, exfiltrate files to the C2 server, and deploy a modified version of the Chisel tunneling program. The path of penetration is still being studied.
As soon as attackers gain access to a new system, they repeat their actions, creating exceptions for Microsoft Defender, installing malware and ensuring its constant activity in the system.
At the end of 2023, TinyTurla-NG was already detected in the networks of Polish NGOs. At that time, Cisco Talos specialists stated that the virus spread through compromised WordPress sites that are used as a command and control server (Command and Control, C2). TinyTurla-NG can execute commands from a C2 server, upload and download files, and deliver scripts to steal passwords from password management databases.

