Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,494
- Points
- 113
Vulnerabilities in state systems give full freedom of action for new malware.
The Chinese hacker group Earth Lusca has been seen attacking government agencies in various countries. Experts from Trend Micro analyzed the new Linux backdoor SprySOCKS, which is used in these attacks.
SprySOCKS is a type of Windows Trochilus RAT Trojan , many of its features have been ported to work on Linux systems. However, the backdoor is a mix of various malicious programs. The management Server Communication protocol (C2 server) is similar to the RedLeaves Trojan, while the interactive shell was adapted from the Linux malware Derusbi .
Earth Lusca remained active throughout the first half of the year, targeting key government agencies in Southeast Asia, Central Asia, the Balkans and other regions of the world. The hackers focused on bodies responsible for foreign policy, technology, and telecommunications.
Attack methods
Hackers exploited several remote code execution vulnerabilities dated between 2019 and 2022, affecting endpoints available on the network. The flaws were used to deploy Cobalt Strike beacons that allow remote access to the target network.
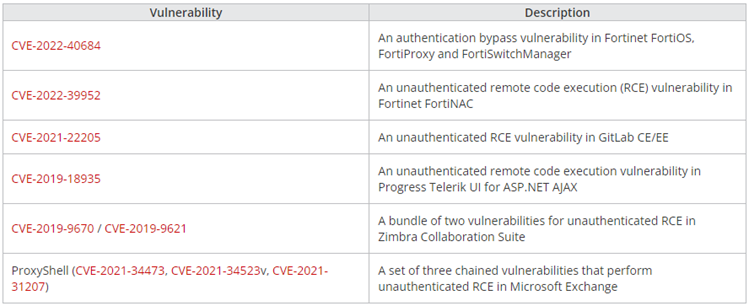
Vulnerabilities used by Earth Lusca
This access was used for Lateral Movement across the network, file and credential theft, and deployment of additional payloads such as ShadowPad.
Technical Details
SprySOCKS uses the high-performance HP-Socket network framework for its operation, and its TCP communications with the C2 server are encrypted using AES-ECB. The main functions of the new malware include collecting system information, launching an interactive shell, managing SOCKS proxies, and basic file manipulation.
Recommendations
It should be a priority for organizations to apply available security updates on publicly available server products, which in this case will prevent the initial compromise from Earth Lusca.
Trend Micro experts note the active development of malware, since two versions of SprySOCKS were discovered: v1.1 and v. 1.3.6.The researchers also point out that the attackers adapted the Linux ELF injector called "mandibule", leaving behind debugging messages and symbols, which may indicate a rush to update the system. software development.
The information highlights the need for continuous monitoring and updating of security systems to protect against increasingly complex and diverse threats in the modern world.
The Chinese hacker group Earth Lusca has been seen attacking government agencies in various countries. Experts from Trend Micro analyzed the new Linux backdoor SprySOCKS, which is used in these attacks.
SprySOCKS is a type of Windows Trochilus RAT Trojan , many of its features have been ported to work on Linux systems. However, the backdoor is a mix of various malicious programs. The management Server Communication protocol (C2 server) is similar to the RedLeaves Trojan, while the interactive shell was adapted from the Linux malware Derusbi .
Earth Lusca remained active throughout the first half of the year, targeting key government agencies in Southeast Asia, Central Asia, the Balkans and other regions of the world. The hackers focused on bodies responsible for foreign policy, technology, and telecommunications.
Attack methods
Hackers exploited several remote code execution vulnerabilities dated between 2019 and 2022, affecting endpoints available on the network. The flaws were used to deploy Cobalt Strike beacons that allow remote access to the target network.

Vulnerabilities used by Earth Lusca
This access was used for Lateral Movement across the network, file and credential theft, and deployment of additional payloads such as ShadowPad.
Technical Details
SprySOCKS uses the high-performance HP-Socket network framework for its operation, and its TCP communications with the C2 server are encrypted using AES-ECB. The main functions of the new malware include collecting system information, launching an interactive shell, managing SOCKS proxies, and basic file manipulation.
Recommendations
It should be a priority for organizations to apply available security updates on publicly available server products, which in this case will prevent the initial compromise from Earth Lusca.
Trend Micro experts note the active development of malware, since two versions of SprySOCKS were discovered: v1.1 and v. 1.3.6.The researchers also point out that the attackers adapted the Linux ELF injector called "mandibule", leaving behind debugging messages and symbols, which may indicate a rush to update the system. software development.
The information highlights the need for continuous monitoring and updating of security systems to protect against increasingly complex and diverse threats in the modern world.

