Brother
Professional
- Messages
- 2,590
- Reaction score
- 533
- Points
- 113
Bypassing email authentication has some very unexpected consequences.
Cybersecurity researcher Timo Longin, in collaboration with SEC Consult discovered a new attack method called "SMTP Smuggling". It allows attackers to send fake emails on behalf of other users, bypassing email authentication.
SMTP (Simple Mail Transfer Protocol) is a standard protocol used for transferring email on the Internet. It describes the rules for exchanging messages between mail servers and clients.
According to experts, the identified problem exploits differences in how incoming and outgoing SMTP servers interpret the sequence of characters indicating the end of email data. Thanks to these differences, an attacker can inject additional information into the email, which will easily bypass SPF, DKIM, and DMARC checks.
In turn, SPF, DKIM, and DMARC are email authentication mechanisms designed to combat spam and phishing. They analyze email headers and help determine whether it was actually sent by the declared sender. However, the SMTP Smug attack can bypass them.
The problem affects millions of domains, including Microsoft, Amazon, PayPal, eBay, GitHub, Outlook, and Office365. In their report, the researchers demonstrated the real possibility of sending emails, in fact, from other people's addresses.
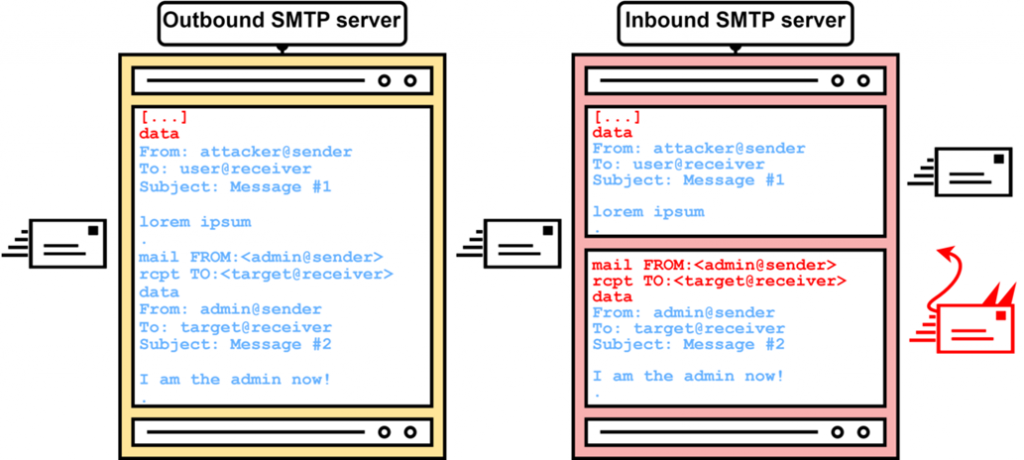
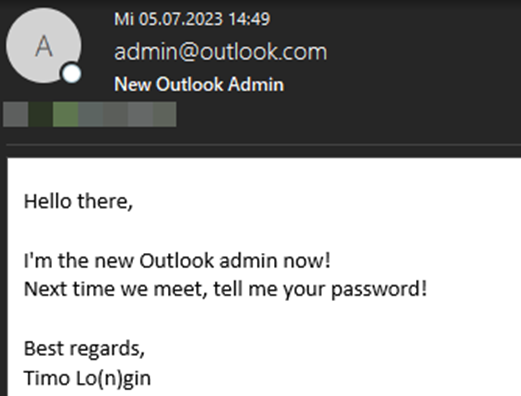
As one of the examples, the researchers used the mailbox "admin@outlook [.] com", which, of course, was not accessible to other specialists. However, the victim of the attack will receive an email from this address. More precisely, this is how the message displays the incoming SMTP server that serves the affected mail service.
In fact, a single email with additional data sewn into it by a potential attacker is interpreted by the vulnerable incoming SMTP server as two different emails. The first one will have the actual email address of the victim, and the second one will have absolutely any address that the attacker wants to use.
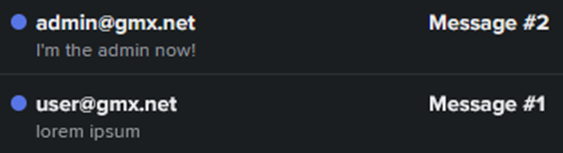
At first glance, it may seem that two simultaneously delivered emails will cause doubts in the potential victim, because she will probably connect them together. However, in fact, the attacker can make the design of emails completely different, and the purpose of the attack is to write it off as a simple coincidence, so the first message will be ignored, but the second one will be viewed.
Vulnerable mail providers were notified of a configuration issue with SMTP server settings at the end of July. GMX fixed the vulnerability in its service in 10 days. Microsoft assigned the problem a medium level of danger and released an update in mid-October. Cisco, in turn, does not consider this a vulnerability at all and does not plan to change the settings yet, which still continues to endanger its customers.
SEC Consult notes that the SMTP Smug attack only helps to bypass authentication. Spam filters can still detect fake emails by their content, but you can hardly rely on spam filters alone.
According to the researchers, it is currently difficult to assess the scale of the threat, since the analysis did not cover all mail servers. There may be other vulnerable configurations.
This vulnerability demonstrates that email authentication protocols are far from perfect and need to be improved to withstand new attack methods. Companies, in turn, should be vigilant and regularly install security updates for their mail servers.
Cybersecurity researcher Timo Longin, in collaboration with SEC Consult discovered a new attack method called "SMTP Smuggling". It allows attackers to send fake emails on behalf of other users, bypassing email authentication.
SMTP (Simple Mail Transfer Protocol) is a standard protocol used for transferring email on the Internet. It describes the rules for exchanging messages between mail servers and clients.
According to experts, the identified problem exploits differences in how incoming and outgoing SMTP servers interpret the sequence of characters indicating the end of email data. Thanks to these differences, an attacker can inject additional information into the email, which will easily bypass SPF, DKIM, and DMARC checks.
In turn, SPF, DKIM, and DMARC are email authentication mechanisms designed to combat spam and phishing. They analyze email headers and help determine whether it was actually sent by the declared sender. However, the SMTP Smug attack can bypass them.
The problem affects millions of domains, including Microsoft, Amazon, PayPal, eBay, GitHub, Outlook, and Office365. In their report, the researchers demonstrated the real possibility of sending emails, in fact, from other people's addresses.

As one of the examples, the researchers used the mailbox "admin@outlook [.] com", which, of course, was not accessible to other specialists. However, the victim of the attack will receive an email from this address. More precisely, this is how the message displays the incoming SMTP server that serves the affected mail service.

In fact, a single email with additional data sewn into it by a potential attacker is interpreted by the vulnerable incoming SMTP server as two different emails. The first one will have the actual email address of the victim, and the second one will have absolutely any address that the attacker wants to use.

At first glance, it may seem that two simultaneously delivered emails will cause doubts in the potential victim, because she will probably connect them together. However, in fact, the attacker can make the design of emails completely different, and the purpose of the attack is to write it off as a simple coincidence, so the first message will be ignored, but the second one will be viewed.
Vulnerable mail providers were notified of a configuration issue with SMTP server settings at the end of July. GMX fixed the vulnerability in its service in 10 days. Microsoft assigned the problem a medium level of danger and released an update in mid-October. Cisco, in turn, does not consider this a vulnerability at all and does not plan to change the settings yet, which still continues to endanger its customers.
SEC Consult notes that the SMTP Smug attack only helps to bypass authentication. Spam filters can still detect fake emails by their content, but you can hardly rely on spam filters alone.
According to the researchers, it is currently difficult to assess the scale of the threat, since the analysis did not cover all mail servers. There may be other vulnerable configurations.
This vulnerability demonstrates that email authentication protocols are far from perfect and need to be improved to withstand new attack methods. Companies, in turn, should be vigilant and regularly install security updates for their mail servers.

