Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,493
- Points
- 113
The new version of the Rilide malware still attacks Chromium-based browsers, steals confidential data and cryptocurrency. However, according to Trustwave experts, this version demonstrates a higher level of complexity due to its modular structure, code obfuscation, and support for the Chrome Extension Manifest V3.
Rilide was first discovered in the spring of 2023. Then Trustwave SpiderLabs researchers said that the malware is aimed at Chromium browsers (including Chrome, Edge, Brave and Opera), disguises itself as a legitimate Google Drive extension and is able to track all the victim's activity, steal cryptocurrency and information, including credentials.
Back then, researchers noted that the upcoming transition to Manifest v3, which defines the capabilities and limitations for extensions in Chromium browsers, may complicate the work of attackers, but this is unlikely to completely solve the problem, since most of the functions used by Rilide will still work.
In a new report, Trustwave analysts report that Rilide has now been updated, and the extension already supports Manifest V3, which allows you to bypass the restrictions associated with the new rules, and also has additional code obfuscation to avoid detection.
Moreover, the malicious extension is now targeting victims ' bank accounts as well. It "learned" to extract stolen data via Telegram and take screenshots at pre-defined intervals, then sending them to the management server.
Currently, Rilide is distributed as part of several malicious campaigns. Since malware is actively advertised and sold on hacker forums, researchers assume that different attackers are behind these attacks. The fact is that Rilide is sold at a price of $ 5,000, but the buyer himself must develop a distribution mechanism.
It is also noted that there have already been several leaks of the Rilide source code on the darknet, and some of them may well have been genuine. As a result, the source code of the malware can be accessed by a wide range of intruders.
One of the detected campaigns targets users of a number of banks, financial service providers, email providers, crypto exchange platforms, VPNs, and cloud service providers. This campaign focuses on users from Australia and the United Kingdom.
Researchers found more than 1,500 phishing pages using typesquatting. Attackers promote them using the SEO poisoning technique in search engines and impersonate real banks and service providers to trick victims into entering their credentials in phishing forms.
Fake page disguised as HSBC Bank
In another campaign, users are attacked through phishing emails purporting to advertise VPN apps and firewalls, such as Palo Alto's GlobalProtect App. In this case, the researchers found a PowerPoint presentation designed for ZenDesk employees, which is disguised as a security warning and directs users to install a malicious extension.

Malicious presentation
The presentation contains slides warning that attackers are impersonating GlobalProtect to distribute malware, and prompts the user to follow these steps to accurately install the real software. In fact, under the guise of "real software" is hiding Rilide.
The third campaign was seen on Twitter. In its framework, victims are directed to phishing sites with fake blockchain games such as P2E (Play To Earn). Installers on these sites distribute the Rilide extension, allowing hackers to steal victims ' cryptocurrency assets.
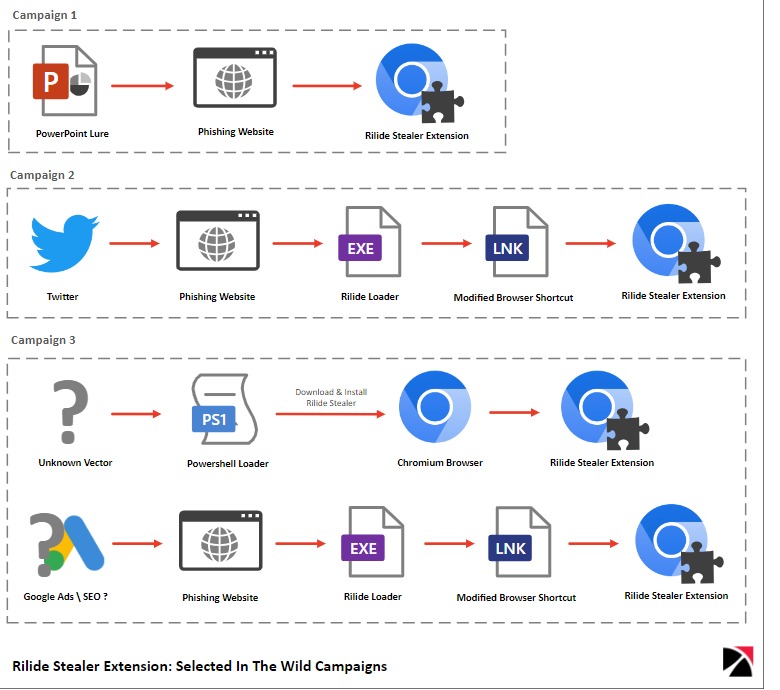
How all the described campaigns work
Regardless of what malicious campaign we are talking about, during installation, the extension communicates with the attackers ' server and receives one of the following commands:
Since Rilide is built on the implementation of remotely hosted JS scripts, its authors had to implement a combination of different methods that circumvent the new Google rules. For example, the new version of the extension uses inline events to execute malicious JavaScript and abuses the Declarative Net Requests API to bypass the XSS prevention mechanism and Content Security Policy (CSP)bans
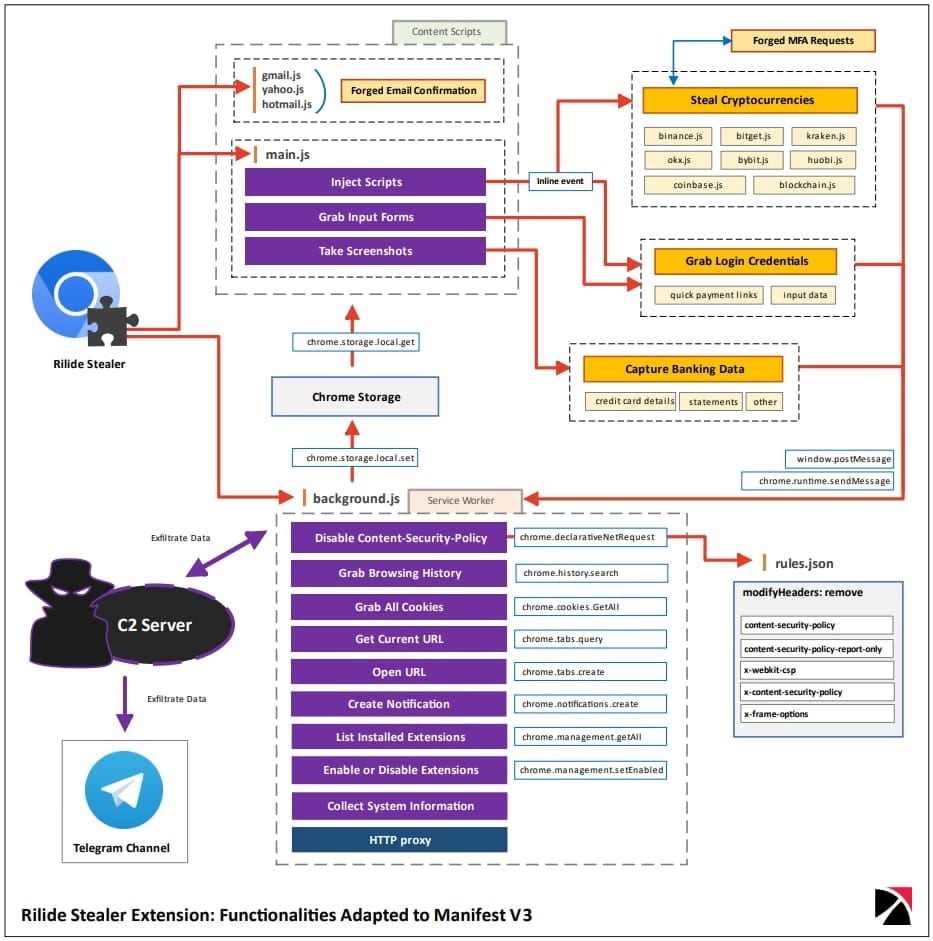
Adapting to Manifest V3
Since Rilide is not distributed through the official Chrome Web Store, where Manifest V3 rules are strictly enforced, malware authors can use workarounds to execute remotely hosted code.
(c) https://xakep.ru/2023/08/04/new-rilide/
Rilide was first discovered in the spring of 2023. Then Trustwave SpiderLabs researchers said that the malware is aimed at Chromium browsers (including Chrome, Edge, Brave and Opera), disguises itself as a legitimate Google Drive extension and is able to track all the victim's activity, steal cryptocurrency and information, including credentials.
Back then, researchers noted that the upcoming transition to Manifest v3, which defines the capabilities and limitations for extensions in Chromium browsers, may complicate the work of attackers, but this is unlikely to completely solve the problem, since most of the functions used by Rilide will still work.
In a new report, Trustwave analysts report that Rilide has now been updated, and the extension already supports Manifest V3, which allows you to bypass the restrictions associated with the new rules, and also has additional code obfuscation to avoid detection.
Moreover, the malicious extension is now targeting victims ' bank accounts as well. It "learned" to extract stolen data via Telegram and take screenshots at pre-defined intervals, then sending them to the management server.
Currently, Rilide is distributed as part of several malicious campaigns. Since malware is actively advertised and sold on hacker forums, researchers assume that different attackers are behind these attacks. The fact is that Rilide is sold at a price of $ 5,000, but the buyer himself must develop a distribution mechanism.
It is also noted that there have already been several leaks of the Rilide source code on the darknet, and some of them may well have been genuine. As a result, the source code of the malware can be accessed by a wide range of intruders.
One of the detected campaigns targets users of a number of banks, financial service providers, email providers, crypto exchange platforms, VPNs, and cloud service providers. This campaign focuses on users from Australia and the United Kingdom.
Researchers found more than 1,500 phishing pages using typesquatting. Attackers promote them using the SEO poisoning technique in search engines and impersonate real banks and service providers to trick victims into entering their credentials in phishing forms.

Fake page disguised as HSBC Bank
In another campaign, users are attacked through phishing emails purporting to advertise VPN apps and firewalls, such as Palo Alto's GlobalProtect App. In this case, the researchers found a PowerPoint presentation designed for ZenDesk employees, which is disguised as a security warning and directs users to install a malicious extension.

Malicious presentation
The presentation contains slides warning that attackers are impersonating GlobalProtect to distribute malware, and prompts the user to follow these steps to accurately install the real software. In fact, under the guise of "real software" is hiding Rilide.
The third campaign was seen on Twitter. In its framework, victims are directed to phishing sites with fake blockchain games such as P2E (Play To Earn). Installers on these sites distribute the Rilide extension, allowing hackers to steal victims ' cryptocurrency assets.

How all the described campaigns work
Regardless of what malicious campaign we are talking about, during installation, the extension communicates with the attackers ' server and receives one of the following commands:
- extension — enable or disable the extension from the list of installed extensions;
- Info — sending information about the system and browser to the management server, collecting all configuration parameters;
- Push — create a notification with the specified message, title, and icon. Clicking on it will open a new tab with the URL received from the hackers management server;
- sCookie — extract all browser cookies and send them to the management server;
- Screenshot - capture the visible area of the currently active tab in the current window;
- URL — create a new tab with the provided URL;
- current_url — get the URL of the active tab;
- History — get all your browsing history for the last 30 days;
- Injections — get the injection code to apply to specific URLs;
- Settings — extract proxy, grabber, and Telegram settings;
- Proxy — enable or disable the proxy, hackers use the CursedChrome implementation, which allows you to view web pages on behalf of the victim;
- screenshot_rules — update the list of rules for capturing screenshots.
Since Rilide is built on the implementation of remotely hosted JS scripts, its authors had to implement a combination of different methods that circumvent the new Google rules. For example, the new version of the extension uses inline events to execute malicious JavaScript and abuses the Declarative Net Requests API to bypass the XSS prevention mechanism and Content Security Policy (CSP)bans

Adapting to Manifest V3
Since Rilide is not distributed through the official Chrome Web Store, where Manifest V3 rules are strictly enforced, malware authors can use workarounds to execute remotely hosted code.
(c) https://xakep.ru/2023/08/04/new-rilide/

