Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113

In this article, we'll take a closer look at what's going on with the iPhone in the forensic lab. We will find out how realistic it is to hack the protection of iOS of different versions and what is needed for this in different cases. We have already described several aspects of this process, but today we will analyze it in full and try to cover all possible options.
On August 13, the BBC Russian Service announced the purchase by the Investigative Committee of iPhone jailbreak equipment, which will open the most recent iPhone in just nine minutes. Do not believe? I also do not believe that such a respectable publication could publish such a thing, but the fact remains.
I would like to comment on the phrase of expert Dmitry Saturchenko: “Israeli Cellebrite needs more than a day to hack an iPhone 12 or 13, and the extracted data requires serious analytics. MagiCube processes the same iPhone in nine minutes, while the equipment is sharpened to receive sensitive data from instant messengers, which contains 80-90% of interesting information. "
An unprepared reader may get the impression that you can just take any iPhone and extract information about the use of instant messengers from it. This is not the case for many reasons. Let's start with the fact that MagiCube is a hard drive duplicator, and another complex analyzes mobile devices. An iPhone is also not suitable for any, but one that runs strictly under the control of iOS 10.0-11.1.2 (that is, it has never been updated after December 2, 2020). Next, we need to find out (from the user) or hack (by third-party solutions - GrayKey or Cellebrite) the lock code. And after that, having unlocked the phone, you can connect it to the Chinese complex and retrieve information.
Despite this, the news spread throughout the mass media. "Specialists" from SecurityLab, without bothering to either put a link to the source, or even indicate the author, write: "The Investigative Committee purchased equipment to gain access to the correspondence." "According to experts, it takes about ten minutes for the MagiCube complex to crack the latest iPhone models."
What happens in the end? Can you jailbreak an iPhone 7 or 8 in nine minutes? Is the iDC-4501 solution (not MagiCube, which is just a hard drive duplicator) really superior to Cellebrite and Grayshift technologies? Finally, how can you jailbreak your iPhone? Let's try to figure out what exactly the Investigative Committee purchased, how and when it works, and what to do in those 99% of cases when the complex does not cope with the task.
It depends ...
Before trying to access an iPhone, let's figure out what can be done and under what conditions. Yes, we had a lot of publications, including very detailed ones, in which we described various ways to hack devices. But here is a black brick in front of you. Which of the many ways and which tools are you going to use? Will it be possible to do this at all, and if it does, how long will it take to hack and what can you expect as a result?Yes, a lot depends on the model of the device and the version of iOS installed on it (which, by the way, you still need to find out - and, looking ahead, I will say: it is far from a fact that you will succeed). But even an iPhone of a completely obvious model with a precisely known version of iOS can be in one of many states, and the set of methods and tools available to you will depend on this.
First, let's agree: we will only consider the generations of iPhones equipped with 64-bit processors, that is, the iPhone 5S models, all versions of the iPhone 6 / 6s / 7/8 / Plus and the current flagship - iPhone X. In terms of jailbreak, these devices are different few (except for older generations if you have access to Cellebrite's services).
Has a lock code been set?
Apple can use the strongest encryption, heap the most complex multi-layered protection, but no one will be able to protect users who have "nothing to hide". If your iPhone does not have a lock code set, extracting data from it is trivial. You can get started in the same nine minutes as mentioned in the BBC article. Probably, the process will take a longer time: it takes about two hours to copy 100 GB of data. What is required for this?First, connect your phone to your computer, establish a trusted relationship, and create a backup. You can even use iTunes for this (be sure to turn off two-way synchronization in it beforehand), but experts will prefer their own software.
Is there a password for the backup?
Not installed? Install and make another backup!
Why set a password for a backup? The fact is that a noticeable part of the information in iOS backups is encrypted even when the user did not set such a password. In such cases, a key that is unique to each device is used for encryption. It is better to set any password you know on the backup; then the backup copy, including the "secret" data, will be encrypted with the same password. Interestingly, you will get access to the protected keychain storage, that is, to all user passwords stored in the Safari browser and many built-in and third-party applications.
But what if the password for the backup is set and you don't know it? Unlikely for people with nothing to hide, but still? For devices running older versions of iOS (8.x - 10.x), the only option is brute force. And if for iOS 8-10.1 the attack speed was acceptable (hundreds of thousands of passwords per second on the GPU), then starting with iOS 10.2 a frontal attack is not an option: the brute-force attack does not exceed hundreds of passwords per second, even when using a powerful graphics accelerator. However, you can try to extract passwords that the user saved, for example, in the Chrome browser on a personal computer, compose a dictionary from them and use it as a basic dictionary for an attack. (Believe it or not: such a simple tactic works in about two cases out of three.)
But devices on iOS 11 and 12 allow you to easily reset your backup password right from the iPhone settings. This will reset some settings, such as screen brightness and Wi-Fi passwords, but all applications and their data, as well as user passwords in the keychain, will remain in place. If there is a lock code, you will need to enter it, but if it is not set, then resetting the password for backup is a matter of a few clicks.
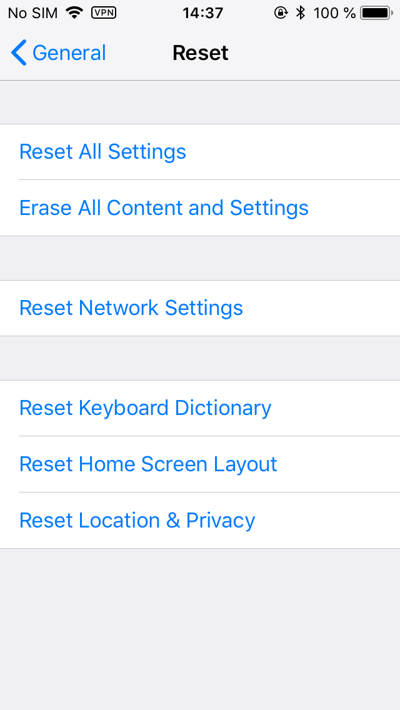
To reset the password for the backup, use the Reset All Settings command. It will reset only some settings, including the backup password, but will not affect the data.
What else can be removed from a device with an empty lock code? Without jailbreaking, you can easily extract the following data set:
- complete information about the device;
- information about the user, Apple accounts, phone number (even if the SIM card was removed);
- list of installed applications;
- media files: photos and videos;
- Application files (for example, iBooks documents);
- system logs crash logs (in them, in particular, you can find information about applications that were subsequently uninstalled from the system);
- the already mentioned backup in iTunes format, which will contain the data of many (not all) applications and user passwords from social networks, sites, authentication tokens and much more.

This is how the interface of an application that retrieves information from an iPhone looks like.
Jailbreak and physical data extraction
If you did not have enough information extracted from the backup, or if you could not guess the password for the encrypted backup, only the jail remains. Now jailbreak exists for all versions of iOS 8.x, 9.x, 10.0–11.2.1 (earlier ones are not considered). There is an Electra jail for iOS 11.3.x that works on earlier versions of iOS 11 as well.To install the jailbreak, you need to use one of the publicly available utilities (Meridian, Electra, etc.) and the Cydia Impactor tool. There are alternative ways of hacking - for example, escalating privileges without installing a public jailbreak by exploiting a known vulnerability (remember, for iOS 10-11.2.1 this is the same vulnerability, information about which, including the ready-made source code, was published by Google specialists). All these methods have a common point: in order to use them, the iPhone must be unlocked and connected to the computer (a trusted relationship has been established).
The next step is to extract the file system image. To do this, at best, it is enough to open a session with the phone via the SSH protocol and execute a chain of commands on the iPhone; in more complex cases, you will need to manually register the necessary paths in the PATH or use a ready-made product. The result will be a TAR file transferred over the tunnel connection.
If your smartphone has iOS 11.3.x installed, you will have to jailbreak it manually, and use the iOS Forensic Toolkit or another similar utility to extract information.
If the iPhone is running iOS 11.4 or a later version, then the jail will have to be postponed indefinitely - until the developer community finds another unpatched vulnerability. In this case, you will serve as a backup (as well as extract common application files, photos and media files and some system logs).
Of course, not everything is backed up. For example, it does not store Telegram correspondence, it does not include e-mail messages, and the history of the user's location data is extremely concise. Nevertheless, a backup is already a lot.
But what if the user is not completely careless and still set the lock code?
Even the most careless users are forced to use Passcode if their employer's security policy requires it or if they want to use Apple Pay. And here there are two options: either the lock code is known or not. Let's start simple.
Is the lock code known?
If you know the lock code, you can do almost anything with the device. Enable and Unlock - Anytime. Change Apple ID password, reset iCloud binding and disable iCloud lock, enable or disable two-factor authentication, save passwords from the local keychain to the cloud and retrieve them from there. For devices with iOS 11 and newer - reset the password for the backup, set your own and decrypt all the same passwords from sites, various accounts and applications.In iOS 11 and later, the lock code, if set, is also required to establish a trusted relationship with the computer. This is necessary both for removing a backup (there may be other options - for example, through the lockdown file), and for installing a jailbreak.
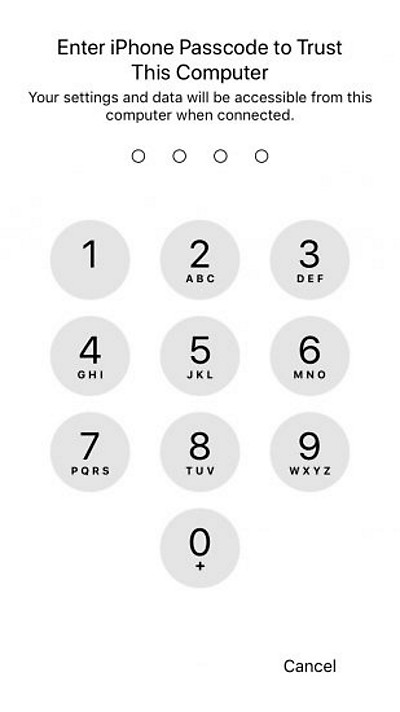
To establish trust between iPhone and computer in iOS 11 and newer, you need to enter a lock code
Will you be able to jailbreak and pull out those few, but potentially valuable data for the investigation that does not end up in the backup? It depends on the iOS version:
- iOS 8.x - 9.x: jailbreak is available for almost all combinations of OS and platforms;
- iOS 10.x - 11.1.2: The jailbreak uses an open exploit discovered by Google. Works on all devices;
- iOS 11.2-11.3.x: jailbreak exists and can be installed;
- iOS 11.4 and higher: jail does not exist at the moment.
What if the lock code is unknown? In this case, the likelihood of successfully extracting at least something begins to decline. However, not all is lost here either - depending on the state in which the phone was submitted for analysis and what version of iOS is installed on it.
Is the device screen locked or unlocked?
The police do not always get a locked phone, for which the lock code is known. The policeman's “request” is quite typical: “Give me the phone. Unblock! "According to the police officers themselves, speaking in a confident tone, and even at the scene, people often fulfill the request. After 10-15 minutes“ they begin to think, ”but it's too late: they will hardly be able to get the unlocked device back.Moreover, the police may have a warrant, which will spell out permission to unlock the device using a fingerprint sensor or the user's face against the will of the owner (but it may not be possible to find out the lock code in the same way, depending on the jurisdiction).Apple has built in iOS protection against such police actions by limiting the period during which Touch ID and Face ID sensors remain functional. After a certain time, which can be counted both from the moment of the last unlocking in general, and from the moment of the last entry of the lock code, the iPhone will offer to enter the lock code the next time it tries to unlock the device.

In the morning, the phone asked to enter the lock code
We will not dwell on this topic in detail, especially since we have already written about it. Suffice it to mention that biometric sensors turn off 48 hours after the last unlock, or after eight hours if the user has not entered the lock code within six days, or after five unsuccessful scan attempts, or after the user activates the SOS mode that appeared in iOS 11.
So, you got into your hands an iPhone, the screen of which is unlocked. Your actions?
- Try to disable automatic screen lock in settings. Note that if your phone has a corporate Exchange or MDM policy, this might be blocked.
- Connect your phone to your computer and try to establish a trusted relationship. For iOS from 8 to 10, it is enough to confirm the Trust this computer request, but for iOS 11 and higher you will need to enter the lock code. If the lock code is unknown, try to find the lockdown file on the user's computer (we have already written about what it is and where it is stored).
- If you succeed in establishing a trusted relationship, create a backup.
- If a trusted relationship could not be established, and the lockdown file was not found or its validity period has expired, you will have to use the GrayKey complex to select the lock code or Cellebrite services (they are provided only to the police and special services of some countries).
Corporate security policy does not allow you to disable automatic blocking. Output? Select a person who will poke the phone so that he does not sleep
You can read more about lockdown files in the article Acquisition of a Locked iPhone with a Lockdown Record . In a nutshell: in order to start communicating with the computer, the iPhone requires a trusted connection, during which a pair of cryptographic keys is created. One of the keys is stored in the device itself, and the second is transferred to the computer, where it is stored as a regular file. If such a file is copied to another computer or slipped onto the phone using special software, then the phone will be sure that it is communicating with a trusted computer. The files themselves are saved here:
- in Windows Vista, 7, 8, 8.1, Windows 10 it is %ProgramData%\Apple\Lockdown. For example:
- in Windows XP it is a file %AllUsersProfile%\Application Data\Apple\Lockdown. The full path will look something like this:
- on macOS, this is a file /var/db/lockdown.
<? xml version = "1.0 ″ encoding =" UTF-8 ″?>
Lockdown files have a limited lifespan in iOS 11 and later and are not known exactly. It was experimentally found that devices that have not been connected to a trusted computer for more than two months sometimes require re-establishment of the trusted relationship, so that old files may not work.
You can get a little more information if you have access to the user's biometrics - his fingerprint or face. Then you can view passwords from the local keychain storage.
Is the iPhone turned on or off?
A lot depends on such a simple thing. If the iPhone is turned on, then there is a great chance that the owner has unlocked the device at least once from the moment it was turned on. This, in turn, means having access to the encrypted user partition - that is, to installed applications and their data, system logs and much more.A phone that has been unlocked at least once runs AFC services, a backup service, and it is possible to get the data to which applications have opened access. Finally, you can extract the photos. For all this, you don't even have to unlock the phone: with some luck, it is enough to use the lockdown file extracted from the user's computer. If there is no such file, you can try to unlock the phone with the Touch ID fingerprint sensor or Face ID.
So, if you get your hands on a turned on iPhone with a locked screen, you can try the following.
- Connect your phone to your computer. If the message Unlock iPhone to use accessories appears on the phone, and the computer does not see the device at all, then you are out of luck: the device is probably running iOS 11.4.1 or newer and more than an hour has passed since the user last unlocked the device. This mode is called USB Restricted Mode and was Apple's reaction to the emergence of services for cracking the lock code - primarily GrayKey and Cellebrite. Alas, if the phone goes into USB Restricted Mode, you will not be able to use the lockdown file or find the lock code using the GrayKey or Cellebrite services. Neither rebooting nor even restoring the firmware via recovery mode with data saving will help. The only option is to unlock the phone using Face ID, Touch ID (about them - below; time, during which you can use biometrics to unlock, is limited). Finally, the phone can always be unlocked by entering the correct lock code.
- If the phone is connected to the computer, then the first thing to do is to get information about the device. Elcomsoft iOS Forensic Toolkit uses the Information command for this. Even without establishing a trusted relationship with the computer, you will be able to find out the iOS version, the exact model ID, the serial number of the device, and possibly the user's phone number (even if the SIM card is removed from the phone). Depending on the version of iOS installed, you will have access to certain ways to get to user data.
- If the phone is connected to the computer, and you have a lockdown file from the user's computer in your hands, consider yourself lucky. Using this file, you can try to create a fresh backup - you don't have to unlock your phone! However, we have already written about lockdown files; if the file is valid, then you will be able to extract from the phone at least extended information about the device (if the iPhone has not been unlocked at least once after turning on). But if the phone was unlocked at least once after it was turned on, then using the lockdown file it will be possible to extract media files (photos and videos), the crash logs, application files, and a fresh backup copy (here is just the password for the backup , if it is installed, it will not be possible to reset - this requires a lock code).
Even if you remove the memory chip from the phone, it will not help you in any way: the data is encrypted, there is no access to it. Moreover, if the iPhone is running iOS 11.4.1 or later, then there is a very high probability that you will not even be able to connect the device to the computer until you enter the correct password. More precisely, you can physically connect it, but data transfer via USB will be blocked - you won't even be able to get information about the device and find out which version of iOS is running on it.
So, you have a locked phone in your hands that you can connect to your computer. Let's try to crack the lock code?
When can you hack the screen lock code?
So we got to the most interesting part. Can you jailbreak an iPhone in nine minutes? And in a day? But in principle? If the phone is locked and the lock code is unknown, much will depend on the state of the device. Let's consider all the possible circumstances in order of increasing complexity.- The phone is running an old version of iOS (up to 11.4) and the phone has been unlocked by the user at least once since the initial boot. In this very favorable environment, you will be able to use GrayKey or Cellebrite's services (if you represent law enforcement). The search speed will be high: a four-digit numeric lock code can be selected in less than an hour, and the six-digit numeric code search speed will be high for the first 300 thousand attempts. Further, the brute-force speed will decrease sharply - the Secure Enclave protection will work.
- The phone is running an old version of iOS (up to 11.4) and the phone never unlocked after being turned on, either iOS 11.4 (it doesn't matter if the phone was unlocked), or iOS 11.4.1 or higher (it doesn't matter if the phone was unlocked, but USB Restricted Mode was not activated - that is, less than an hour has passed since the device was last unlocked, or the phone was connected to a digital adapter to prevent blocking). In all these cases, the search speed will be very slow: four-digit numeric lock codes can be cracked in a week, and a six-digit numeric code can be iterated over up to two years.
- The phone is running iOS 11.4.1 or newer; USB Restricted Mode is activated. Alas, the only thing that can be done in this case is to try to unlock the phone with Touch ID or Face ID, or enter the correct lock code. It will not be possible to start an automated search, just as it will not be possible to bypass data destruction after ten incorrect attempts (if this option is enabled by the user
How lock code cracking works
For modern devices with iOS versions 10 and 11, there are exactly two solutions that allow you to choose a screen lock code. One of them was developed by Cellebrite and provides it as a service that is available exclusively to law enforcement agencies, subject to an appropriate regulation. To crack the lock code, the phone must be sent to the company's service center; and to understand whether brute-force is possible in principle, you will be prompted to run a special utility. Little is known about Cellebrite's solution; the company carefully guards its secrets.Another solution is called GrayKey - it was developed by Grayshift. The solution is supplied to law enforcement agencies and some other organizations that can independently brute-force passwords. We know more about GrayKey.
The Grayshift solution does not use DFU mode (it was through it that old iPhones were hacked) and loads the agent in system mode. The brute-force attack can be launched both on devices that were unlocked at least once after turning on or restarting, and on "cold" devices that were just turned on. At the same time, the search speed differs not even several times - by orders of magnitude.
So, for a device that was unlocked at least once after booting, a full search of all four-digit passwords is possible in 30 minutes, but for the same device, if it was just turned on, an attack on a four-digit code will last up to 70 days, and you can forget about cracking six-digit digital passwords without a high-quality dictionary: a complete search will take decades (the device only gives one attempt every ten minutes). True, there is a subtlety with six-digit codes: after 300 thousand attempts, the search speed drops sharply and the device goes into slow search mode.

Grayshift presentation slide
Sounds good (or bad, depending on your point of view)? Alas, “fast” search is possible only for iOS versions up to 11.3.1 inclusive. If a user has updated their iPhone at least once after May 29, 2018, then the device will run iOS 11.4 or later. There, "quick" brute-force with the help of GrayKey is impossible. For iOS 11.4 and newer, the GrayKey brute force is limited to one password per ten minutes. This means that a device with a six-digit numeric lock code (and modern versions of iOS offer this code to be set by default) will be almost impossible to hack.
USB Restricted Mode
This mode has already been written about many times, including on the pages of our magazine. Starting with iOS 11.4.1, iPhone and iPad devices completely block USB communication one hour after the device was unlocked or disconnected from the accessory. Most likely, this mode was introduced in order to counter the GrayKey and Cellebrite complexes, which allow you to guess the device lock code using an unknown Apple exploit. The mode turned out to be quite effective: devices with a blocked port cannot be connected to the corresponding system, and the search does not start.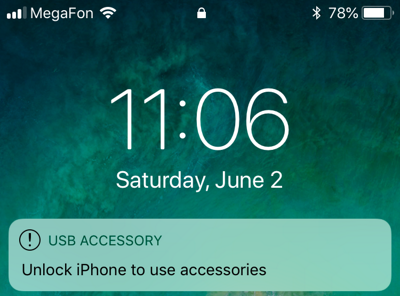
This is what the iPhone screen looks like if you try to connect it to a computer or accessory an hour after the screen is locked or disconnected from a computer or accessory
Is it possible to bypass USB protection mode? Firstly, to activate data transfer, it is enough to unlock the phone, for example, using a fingerprint (which, in turn, is also not eternal - see above). Secondly, the activation of the restriction can be prevented by connecting the phone before the expiration of an hour from the moment of the last locking to a compatible accessory (not all are suitable!), Even in a locked state.
In other words, if the devices are confiscated, the police officer will not only have to put the phone in the Faraday cage, but also connect it to a compatible accessory (for example, the official Apple Lightning to USB 3 adapter with an additional port with charging support will do). If this is not done, then in just an hour the phone will go into protective mode and it will not be possible to start brute-force lock codes.
Safety is a never-ending race. Apple is aware of the possibility of bypassing USB Protective Mode and is developing technology that will block data transfer immediately after the device is locked. If this feature is included in the next iOS build (and this is not a fact), then data transfer via the USB protocol will be automatically deactivated immediately after the device screen is locked - you will have to connect the phone to the accessories or the computer in an unlocked state.
For the sake of user convenience, exceptions have been made for the adapter to the audio jack (however, its connection does not affect the operation of USB Restricted Mode in any way) and for charging from ordinary chargers - but not from a computer port.
What to do if the phone is locked, broken or not at all
How can you retrieve data from a locked or broken device? Much the same as from a device that does not exist at all: through the iCloud cloud. Police may request all data from a user account, including cloud backups, from Apple if instructed to do so. For everyone else, another method is available: using the Apple ID and user password.Where do I get my Apple ID and password? You can, for example, run Elcomsoft Internet Password Breaker on the user's computer and see if there is a password from Apple ID or iCloud (it will be the same). Or try to reset it via mail. You can bypass two-factor authentication, if it is activated, by receiving an SMS to the SIM card removed from the same iPhone.
Finally, you can look for the so-called authentication token on the user's computer, which will allow you to log in to iCloud without a username, password, and secondary authentication factor. Of course, both the authentication token and the password from Apple ID or iCloud may not be found in every case, and the SIM card can be protected by its own PIN, but if you managed to bypass these obstacles, then using specialized software (for example, Elcomsoft Phone Breaker) you can download the following things:
- cloud backups (up to two for each device in the account);
- synchronized data. Here is the expanse: the list of pages open in Safari with the history of visits, and calendars, and notes, and contacts, and even the call log and all text messages, including iMessage (for iMessage, however, you will need both a password and a lock code for one of the user's trusted devices). If the user has a Mac, there may be files synced from the computer, and even the escrow key to decrypt the FileVault 2 partition;
- if iCloud Photo Library is turned on, then photos;
- if iCloud Keychain is enabled, then the user's passwords from various online resources. To do this, you will need to enter the lock code for one of the user's trusted devices
Conclusion
If you read this article, you probably already guessed whether it is possible to jailbreak an iPhone in nine minutes using a "magic cube" or a specialized unnamed complex for jailbreaking mobile devices. Yes, you can - if the phone is running iOS 10-11.2.1 (that is, it has not received the update to iOS 11.2 released on December 2, 2017) and has been kindly unlocked by a suspect, is not protected by a lock code, or the lock code is known.If the user has updated the device at least once after December 2 of last year, the magic will not work. If the phone is locked with an unknown password, the magic will not work, the lock code will have to be cracked with a separate GrayKey or Cellebrite solution (which, by the way, if successful, will extract all the data on its own) ... If the phone is locked and is running the latest version of iOS 11.4.1, and more than an hour has passed since the last unlocking or connection to an accessory, then these services will not help either.
What is the likelihood that the phone is running iOS 11.4.1? According to independent sources (Apteligent and StatCounter), iOS 11.4.x accounts for 61 to 63% of devices. Unfortunately, sources do not distinguish between iOS 11.4 and 11.4.1, but historical data suggests that the share of iOS 11.4.1 at the end of August 2018 is about 57%. We can say with confidence that these 57% of devices today will be impossible to hack solely by technical means, without forcing the user to unlock the device or provide the lock code.
What is expected in the near future? IOS 12 is coming soon, which is likely to be used by almost all iOS 11 users and most users of older devices: the new version of the system is really faster than the previous ones. Some reviewers even describe the beta versions with the words "new life for old devices", and there is a significant amount of truth in this. In particular, the massive transition to iOS 12 means the massive distribution of USB Restricted Mode.
A vulnerability has already been found and confirmed for iOS 11.4. Jailbreak can be expected from day to day. No vulnerabilities have yet been found for iOS 11.4.1, but we rate the likelihood that they will be found as high. True, you have to wait.
Critical vulnerabilities have not yet been identified in beta versions of iOS 12, but we also believe the likelihood of their detection is high.
(c) xakep.ru

