Hacker
Professional
- Messages
- 1,041
- Reaction score
- 851
- Points
- 113
The secrecy of correspondence has been in trend since the days of the Roman Empire, when the first ciphers were invented to transmit important information. Over the years, this topic is gaining more and more popularity. And the protection of e-mail is becoming important not only for special agents and intelligence officers, but also for ordinary people. Since we often send important information, which may contain data on which hackers can easily empty your virtual wallet and more.This article was written for educational purposes only. We do not call anyone to anything, only for information purposes! The author is not responsible for your actions
Why email protection is needed
There are a lot of sites and services that vow to protect the privacy of their users from any encroachments. True, often - only in words. For example, the ProtonMail protected mail service has already been repeatedly accused of helping law enforcement agencies and leaking information about its users into the wrong hands (the first time - in 2018, the second - quite recently). Every time the postal's management found excuses for itself, but there is no smoke without fire, as they say. This means that you need to worry about protecting e-mail and anonymity yourself, not relying on other people's uncles and aunts. What is needed for this? But right now we'll figure it out.

Email protection
As always, this post will contain the necessary part of the theory, and then I'll talk about some of the applications and explain what they are for and how to use them. Unless, of course, you die of boredom studying the first part of the opus. Let's go?
(Not) boring theory
Even a small child, just out of diapers, is already well aware that Windows, in terms of the reliability of storing personal data, resembles a sieve. Therefore, if you do not have the opportunity to forever get rid of this product of programmers from Redmond (otherwise what will we run our favorite toys on?), The system needs to be configured correctly, forever discouraging it from transferring whatever is not needed anywhere. Competent Windows setup is a topic for a separate conversation, and we will definitely return to it someday, but now we are talking about something else.
After we install a secure OS that does not tell its creators about our every step, we need to think about the connection with the outside world. The most ancient and widespread way of such communication after pigeon mail is e-mail. It is not easy to do without it: it would, of course, be nice if all kinds of robots sent us confirmation of registration somewhere in a forbidden telegram, but for some reason they prefer to do it with “soap”, as if in the Stone Age.
You need to understand that if the e-mail server does not belong to you personally, is not on your mezzanine next to your grandmother's galoshes and a box of grandfather's pills for flatulence, and, among other things, open source software does not run on it, then there is no guarantee that your correspondence will not Comrade Major is reading or is not filtering by keywords by a specially trained robot. Despite the fact that the statements of the company - the owner of the server about its honesty, whiteness and fluffiness, you, with all your desire, can not check in any way.
Even if the email service encrypts your data on the fly right in the browser, the encryption algorithm is still downloaded from the server. How do you check the correctness of this very algorithm every time you send a letter? Conclusion: no matter whoever owns the mail service, we certainly cannot trust him with our letters. From this it follows that the responsibility to encrypt letters lies with us.
You can send and receive mail via the web interface, but in this case you lose the pleasure of using proven third-party open source plugins designed to ensure privacy. Therefore, our choice is a mail client.The requirement for any application that operates on your data or is responsible for protecting it is always the same: the source code of this application must be open. This is the bare minimum that can provide protection against bookmarks and undocumented features. All applications and plugins presented in this article are open source.
I recommend installing Thunderbird, for example. Firstly, no comrade major will pronounce this name without mistakes the first time, and secondly, the software is supported by the community and allows you to install extensions. To encrypt correspondence, you can use the Enigmail plugin, which is actively developed to this day and is regularly updated.
In addition, we need special applications that implement encryption - this is GnuPG for * nix or Pgp4Win for Windows. After that, it will be necessary to create a private - public key pair and do not forget to sign your letters with an electronic signature so that the recipient knows for sure that the letter came from you. Sounds complicated? In fact, everything is much simpler than it seems.
Even taking into account encryption, the mail server will still know where you connected to it from, it will be able to determine the connection time, actions with letters (delete, create, forward) and the address to which the letter was sent. But only the recipient can read the information from the letter. And don't forget, the subject line header is not encrypted by default, so choose your subject carefully so you don't get caught up in accident.
Installing and configuring the necessary tools
You should definitely not have any problems installing the Thunderbird mail client - according to rumors, once even a chimpanzee from the Ryazan zoo coped with this daunting task. Next, let's install Pgp4Win, just make sure that the "Components of the installed program" screen contains all the necessary checkboxes!
After that, launch Thunderbird and configure access to your mailbox in the client (documentation on configuring Thunderbird on the Internet in bulk). The next step is to install the Enigmail plugin.
Having finished these dance numbers with a tambourine, we create a key pair (public and private key) and a key revocation certificate. This certificate will be required if one day you lose the secret key due to drunkenness for some reason and you need to revoke the public key uploaded to the server.
So, to create a key pair, go to the menu "Enigmail → Key Manager". After that, you need to select the "New key pair" item in the "Create" menu. In the window that opens, the settings for the key pair to be created, the field for entering a passphrase and the choice of encryption algorithms in the "Advanced" tab will be displayed. The program offers to choose one of two cryptographic algorithms - ECC and RSA.
Choosing between ECC and RSA
Let's see how these algorithms differ from each other and which one is better to choose.
RSA (an abbreviation for the names of the creators - Rivest, Shamir and Adleman ) is an asymmetric cryptographic algorithm based on the complexity of the problem of factoring (decomposing) large integers. It was an abstruse quote from Wikipedia. To put it simply, it is enough to say that this algorithm is old, like Pentium 4, but just as reliable and time-tested. It is used ubiquitously in a wide variety of applications and secure protocols.
There is a newer and, it is believed, progressive analogue - the ECC (Elliptic Curve Cryptography) algorithm. The same Wikipedia tells us that this asymmetric algorithm "relies on elliptic curves over finite fields." What this means, if you wish, you can read in the same place. What is important for us is this: to ensure the same degree of cryptographic strength, the RSA algorithm requires keys with a length of 4096 bits, while the ECC algorithm requires only 256 to 384 bits. And if we take ECC with a key length of 521 bits, then in terms of cryptographic strength it will be equivalent to RSA with a key length of 15 360 bits!
From this it follows that encryption using ECC will be faster and less energy-intensive, which is good news if you use mobile devices. On the other hand, with RSA, we use a time-tested (and a lot of mathematicians) cryptographic algorithm, which also has a certain "margin of safety" before the advent of the era of quantum computers.
Password is important for protecting your email
Despite the strength of the cryptoalgorithms, attention must be paid to choosing a high-quality encryption password. If the password is not strong enough, then it will not be difficult to decrypt your correspondence, no matter how cool crypto algorithms you use.
Don't forget: the password must not be short - you must use at least 12-15 characters. The password should not be any dictionary word, it should have numbers and letters of both registers, an introduction, conclusion, development of a dramatic plot and a list of used literature at the end.
Basically, the rule works: the easier it is for you to remember the password, the easier it will be for an attacker to pick it up. Therefore, you can just bang your forehead on the keyboard a couple of times, and then learn the resulting pseudo-random sequence of characters. The main thing is to never invent or change passwords after a noisy party. Once you break this rule, you will understand why.
After successfully creating a key pair, the program will prompt you to create a revocation certificate. I recommend doing this just in case.
Everything is now ready. If someone wants to encrypt correspondence with you, they will need a public key. You can transfer it to the interlocutor in any way - after all, if the public key is intercepted, then there will still be no way to decrypt the correspondence. But still, I recommend uploading the public key to a special server - the key server. From there, anyone can retrieve your public key, for example by searching for a postal address. To upload a key to the server, in the Key Management snap-in, in the program menu, select Place public keys on the key server.
After that, the key will be automatically uploaded to the server.
Now let's take a look at what it is like protecting email with asymmetric cryptography. We will create and send ourselves an encrypted message and see how it looks with and without the Enigmail plugin - as if we were intercepting someone's message. We have everything set up, we just need to create a letter in the usual way, not forgetting to click on the "Encrypt" and "Sign" buttons.
The received message will look like the picture below.
Received a letter!
Here you can see that the message has been decrypted and its signature has been verified, which is what Enigmail informs us about.
What if we don't know the secret key and just intercepted this message, for example, on the mail server? How it will look in this case, you can see in the next picture.
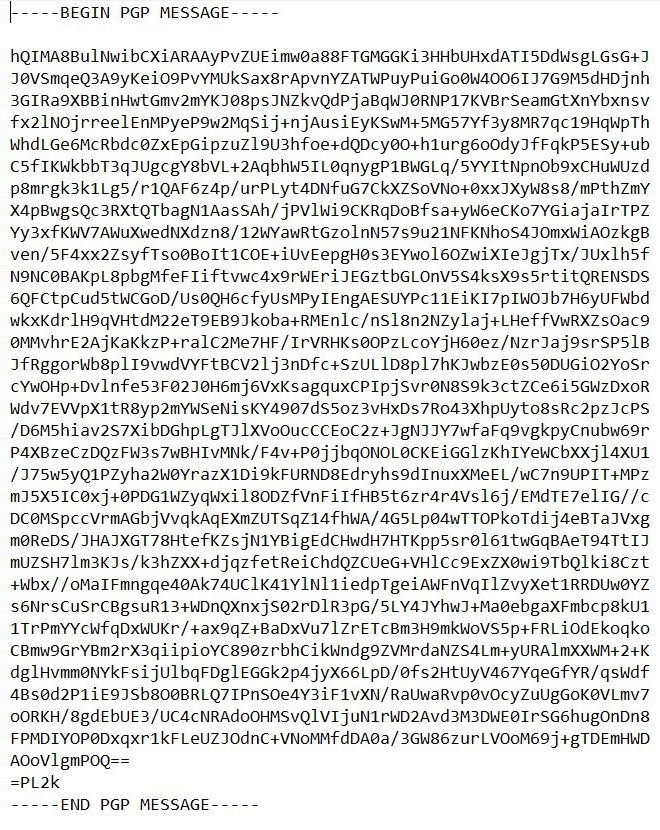
This is what the ciphertext of our letter looks like.
As you can see, whoever intercepts our mail will have big problems reading it.
Protecting email with the Mailvelope plugin
What if, for some reason, you don't want to install an email client, but still decide to protect your correspondence? There is a way out: a browser extension called Mailvelope. It is open source, supported by all modern browsers, and does not require any third-party applications to run. But if you install Pgp4Win on your computer, then you will have the opportunity to choose which engine to use - GnuPG or OpenPGP.js. The latter implements PGP encryption in JavaScript .
To start using email encryption with Mailvelope, you will also need to generate a key pair and send the public key to the key server - in the Mailvelope settings, this can be done by checking the desired checkbox.
The generated key pair will appear in the Key Management tab.
In addition, there is the ability to import and export ready-made key pairs. The extension can also encrypt transmitted attachments and individual files, it has the ability to add an electronic signature. Now, if you go to your mailbox through the web interface and try to write a letter to someone, a new button will appear in the letter entry form that launches Mailvelope.
If you click on this button, a message entry window will open. When the letter is written, you must click on the "Encrypt" button.
The encrypted message will be automatically copied to the web interface of the mail server.
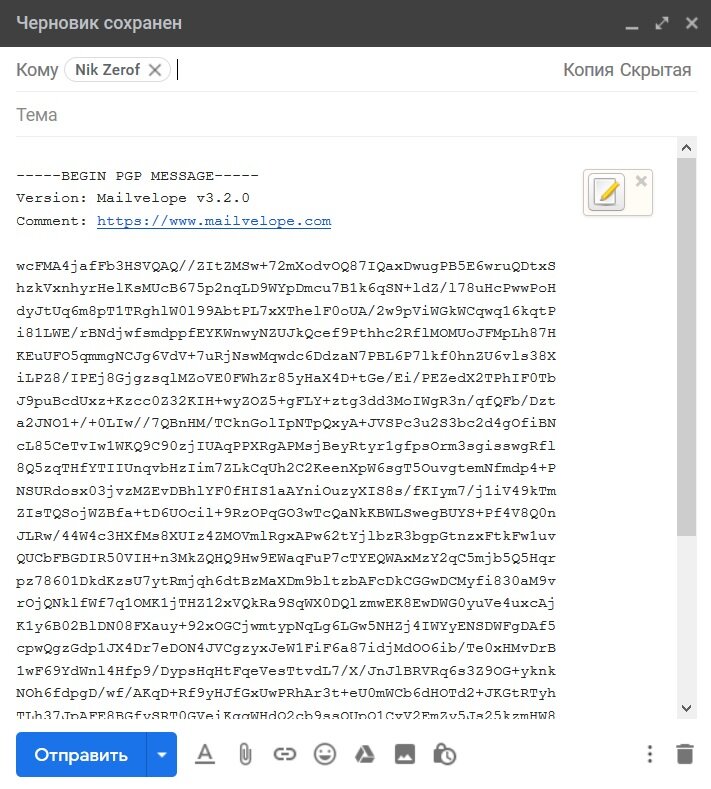
We inserted the ciphertext into the mail server interface.
If the extension is active, the message is decrypted and the electronic signature is automatically verified, you only need to enter your password.
Email encryption on Android
If you have an Android smartphone, check out the OpenKeychain app to help you encrypt messages on your phone. As a mail client for Android, you can use K-9 Mail - this is a well-known open source mail client, and the principle of generating key pairs there is exactly the same as on the desktop.
Now you know how to ensure the protection of e-mail and the transfer of confidential information through an untrusted network - the Internet, where everyone, from the provider to the administrator of the mail server, can intercept and read your emails and find out all the secrets.
Using asymmetric cryptography, you can safely transfer, for example, keys for decrypting encrypted containers that you left on some file hosting service, and any other non-public data.
cryptoworld.su

