Father
Professional
- Messages
- 2,602
- Reaction score
- 837
- Points
- 113
Are hardware keys really more secure than passwords?
A new Verizon Data Breach Investigation Report indicates that almost 30% of all recorded violations over the past 10 years were caused by stolen credentials. This trend highlights how critical the role of passwords and other authentication tools has become in today's digital threats.
Therefore, at the moment there is an increased interest in modern authentication methods, such as FIDO2. This standard uses unique cryptographic identities associated with hardware devices such as smartphones or PCs. Instead of traditional passwords, it uses biometric data and multi-factor authentication via Single Sign-On (SSO) technology.
However, Silverfort stated in its research that even such protective measures can be circumvented. The Silverfort technique, based on a Man-in-the-Middle (MitM) attack, allows you to intercept and copy user sessions in various applications that use SSO solutions.
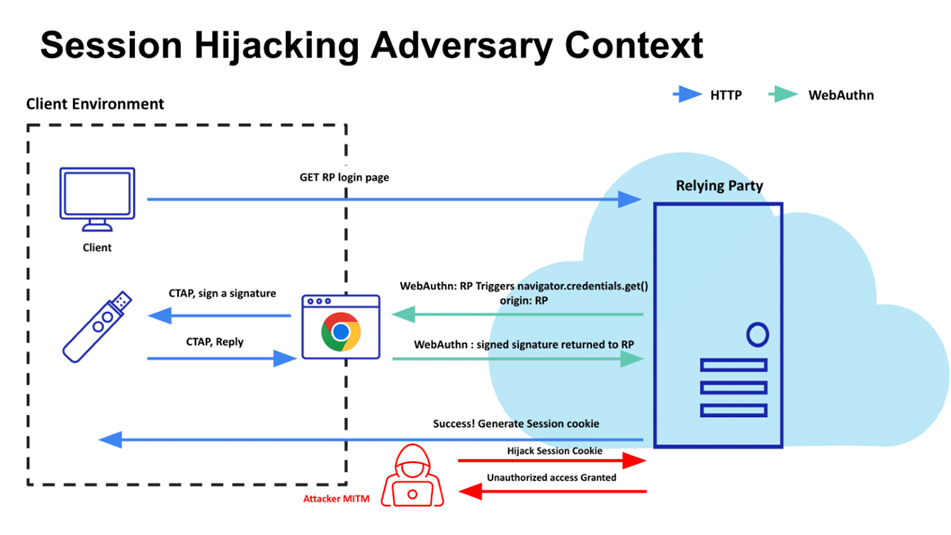
Intercepting an authentication session
FIDO2 is designed to protect against phishing and MITM attacks by replacing vulnerable passwords with more reliable hardware keys and biometrics. However, this solution depends on external systems such as SSO, which create authentication sessions that serve as a bridge between the user and the application. The problem is that the protection provided by protocols like Transport Layer Security (TLS) does not apply to tokens and sessions that can persist and be accessed by the clock.
According to Silverfort, a successfully authenticated session can transmit sensitive data, and the session token can be copied and used repeatedly without restrictions. It is noted that after passing authentication, the user gets almost unlimited access to resources, which increases the risk of abuse.
The researchers emphasize that while their methods reveal some weaknesses in the processes, standards like FIDO2 are still significantly superior to passwords and knowledge - based forms of personal data protection.
The FIDO Alliance stressed that the circumvention methods described in the study are technically correct, but do not reflect vulnerabilities in the FIDO authentication standards. The problem is the industry's inability to develop a unified approach to protecting authentication tokens from theft or abuse.
However, the "token binding" solution can solve this problem, but the widespread adoption of such technology is still limited, and the only major browser that supports it is Microsoft Edge.
Token binding works by adding an additional layer of security by binding the session authentication token to the underlying TLS handshake, which is used to encrypt traffic on the external interface. In practice, this means that only a real user will be able to use the token to access applications, and an attacker will not be able to duplicate the session to save their access.
Back in 2022, Microsoft added support for password-free login using Windows Hello and FIDO2 security keys to Azure AD. And starting in 2021, GitHub users can protect their accounts with FIDO2 hardware security keys.
A new Verizon Data Breach Investigation Report indicates that almost 30% of all recorded violations over the past 10 years were caused by stolen credentials. This trend highlights how critical the role of passwords and other authentication tools has become in today's digital threats.
Therefore, at the moment there is an increased interest in modern authentication methods, such as FIDO2. This standard uses unique cryptographic identities associated with hardware devices such as smartphones or PCs. Instead of traditional passwords, it uses biometric data and multi-factor authentication via Single Sign-On (SSO) technology.
However, Silverfort stated in its research that even such protective measures can be circumvented. The Silverfort technique, based on a Man-in-the-Middle (MitM) attack, allows you to intercept and copy user sessions in various applications that use SSO solutions.

Intercepting an authentication session
FIDO2 is designed to protect against phishing and MITM attacks by replacing vulnerable passwords with more reliable hardware keys and biometrics. However, this solution depends on external systems such as SSO, which create authentication sessions that serve as a bridge between the user and the application. The problem is that the protection provided by protocols like Transport Layer Security (TLS) does not apply to tokens and sessions that can persist and be accessed by the clock.
According to Silverfort, a successfully authenticated session can transmit sensitive data, and the session token can be copied and used repeatedly without restrictions. It is noted that after passing authentication, the user gets almost unlimited access to resources, which increases the risk of abuse.
The researchers emphasize that while their methods reveal some weaknesses in the processes, standards like FIDO2 are still significantly superior to passwords and knowledge - based forms of personal data protection.
The FIDO Alliance stressed that the circumvention methods described in the study are technically correct, but do not reflect vulnerabilities in the FIDO authentication standards. The problem is the industry's inability to develop a unified approach to protecting authentication tokens from theft or abuse.
However, the "token binding" solution can solve this problem, but the widespread adoption of such technology is still limited, and the only major browser that supports it is Microsoft Edge.
Token binding works by adding an additional layer of security by binding the session authentication token to the underlying TLS handshake, which is used to encrypt traffic on the external interface. In practice, this means that only a real user will be able to use the token to access applications, and an attacker will not be able to duplicate the session to save their access.
Back in 2022, Microsoft added support for password-free login using Windows Hello and FIDO2 security keys to Azure AD. And starting in 2021, GitHub users can protect their accounts with FIDO2 hardware security keys.

